Microsoft has raised the alarm today about a new malware strain that infects users’ devices and then proceeds to modify browsers and their settings in order to inject ads into search results pages.
Widespread malware campaign seeks to silently inject ads into search results, affects multiple browsers – Microsoft 365 Defender Research Team
Named Adrozek, the malware has been active since at least May 2020 and reached its absolute peak in August this year when it controlled more than 30,000 browsers each day.
Such a sustained, far-reaching campaign requires an expansive, dynamic attacker infrastructure. We tracked 159 unique domains, each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique, polymorphic malware samples on average. In total, from May to September 2020, we recorded hundreds of thousands of encounters of the Adrozek malware across the globe, with heavy concentration in Europe and in South Asia and Southeast Asia. As this campaign is ongoing, this infrastructure is bound to expand even further.
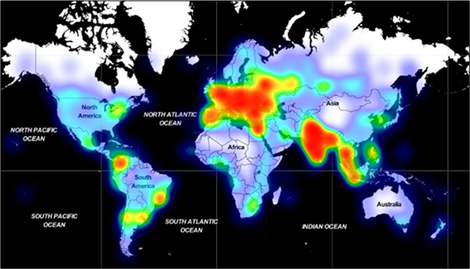
Based on internal telemetry, the highest concentration of victims appears to be located in Europe, followed by South and Southeast Asia.
How ADROZEK spreads and works
Microsoft says that, currently, the malware is distributed via classic drive-by download schemes. Users are typically redirected from legitimate sites to shady domains where they are tricked into installing malicious software.
Attackers use this sprawling infrastructure to distribute hundreds of thousands of unique Adrozek installer samples. Each of these files is heavily obfuscated and uses a unique file name that follows this format: setup_<application name>_<numbers>.exe.
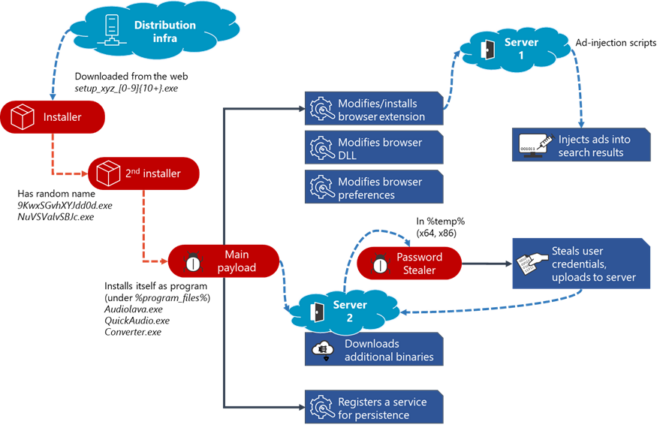
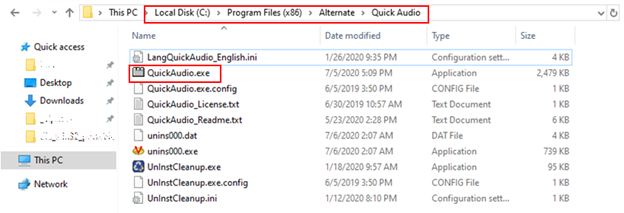
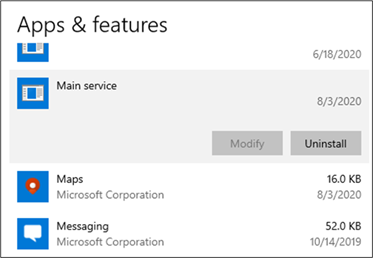
When run, the installer drops an .exe file with a random file name in the %temp% folder. This file in drops the main payload in the Program Files folder using a file name that makes it look like a legitimate audio-related software. We have observed the malware use various names like Audiolava.exe, QuickAudio.exe, and converter.exe. The malware is installed like a usual program that can be accessed through Settings>Apps & features, and registered as a service with the same name.
The boobytrapped software installs the Androzek malware, which then proceeds to obtain reboot persistence with the help of a registry key.
Once persistence is assured, the malware will look for locally installed browsers such as Microsoft Edge, Google Chrome, Mozilla Firefox, or the Yandex Browser.
If any of these browsers are found on infected hosts, the malware will attempt to force-install an extension by modifying the browser’s AppData folders.
To make sure the browser’s security features don’t kick in and detect unauthorized modifications, Adrozek also modifies some of the browsers’ DLL files to change browser settings and disable security features.
Modifications performed by Adrozek include:
- Disabling browser updates
- Disabling file integrity checks
- Disabling the Safe Browsing feature
- Registering and activating the extension they added in a previous step
- Allowing their malicious extension to run in incognito mode
- Allowing the extension to run without obtaining the appropriate permissions
- Hiding the extension from the toolbar
- Modifying the browser’s default home page
- Modifying the browser’s default search engine
All of this is done to allow Adrozek to inject ads into search results pages, ads that allow the malware gang to gain revenue by directing traffic towards ad and traffic referral programs.
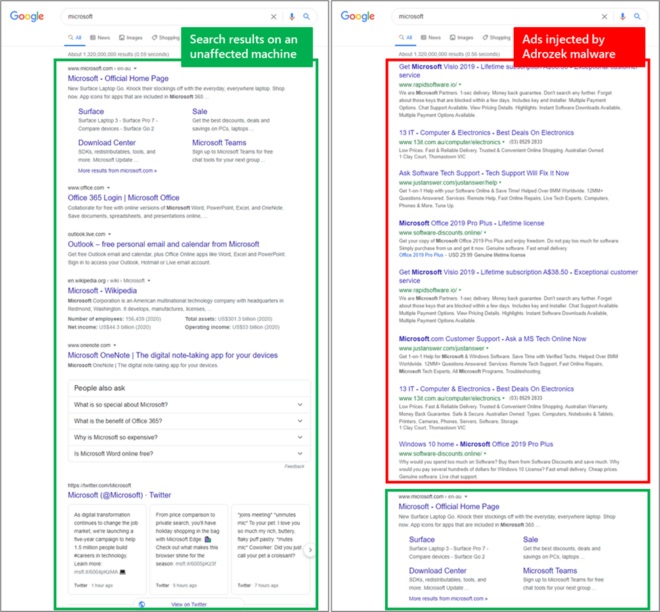
But if this wasn’t bad enough, Microsoft says that on Firefox, Adrozek also contains a secondary feature that extracts credentials from the browser and uploads the data to the attacker’s servers.
A MASSIVE OPERATION EXPECTED TO GROW EVEN FURTHER
Microsoft says the Adrozek operation is extremely sophisticated, and especially in regards to its distribution infrastructure.
The OS maker said it tracked 159 domains that hosted Adrozek installers since May 2020. Each domain hosted on average 17,300 dynamically-generated URLs, and each URL hosted more than 15,300 dynamically-generated Adrozek installers.
“While many of the domains hosted tens of thousands of URLs, a few had more than 100,000 unique URLs, with one hosting almost 250,000. This massive infrastructure reflects how determined the attackers are to keep this campaign operational,” Microsoft said.
“The distribution infrastructure is also very dynamic. Some of the domains were up for just one day, while others were active for longer, up to 120 days.”
All in all, due to its prolific use of polymorphism to constantly rotate its malware payloads and distribution infrastructure, Microsoft expects the Adrozek operation to grow even more in the coming months.
“End users who find this threat on their devices are advised to re-install their browsers,” Microsoft said today.
Ref: Microsoft



